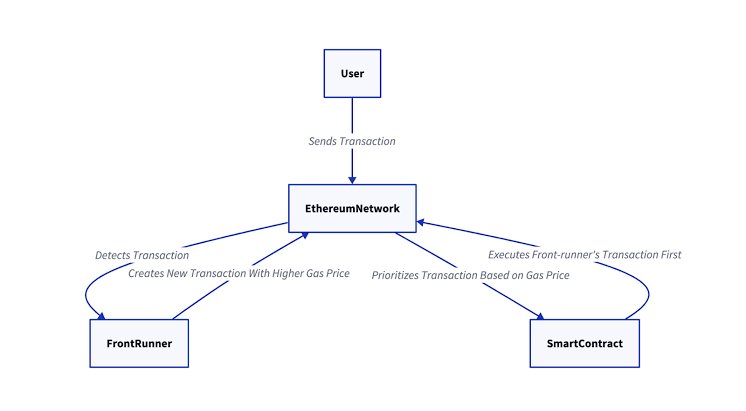
In traditional finance, front-running is illegal. In DeFi, it's a technical vulnerability of how public blockchains and automated market makers (AMMs) like Uniswap work.
⚙️ How Front-Running Works in DeFi
1. User A submits a large trade on a DEX (e.g., buying a token).
2. That transaction is broadcast to the mempool (a public waiting area for pending transactions).
3. A bot or attacker scans the mempool and sees the trade.
4. The attacker submits their own buy order with higher gas fees so that their transaction is mined before User A’s.
5. The attacker sells the token right after User A’s trade, taking advantage of the price increase User A caused.
This is also called a "sandwich attack", a specific form of front-running.
🥪 Example: Sandwich Attack
Step 1: Front-run – Attacker sees a user about to buy Token X and submits a buy order just before.
Step 2: User’s transaction – User A buys Token X, pushing the price up.
Step 3: Back-run – Attacker sells Token X at the higher price, pocketing the difference.
💰 Why It's Profitable
- Because DEXs like Uniswap use Automated Market Makers (AMMs), large trades shift the price (slippage). Front-runners exploit this to:
- Buy low (before price goes up)
- Sell high (after price goes up due to victim’s trade)
📉 Consequences for Users
- Worse execution prices
- Increased slippage
- Unfair market behavior
- Loss of value for large or slow trades
🛡️ How to Prevent Front-Running
1. Use Slippage Protection
Set low slippage limits on DEX trades to avoid being sandwiched.
2. Private Transactions
Use tools like Flashbots, MEV-Blocker, or Eden Network to bypass public mempools.
3. Transaction Bundling
Services like CoW Swap bundle orders to protect users from MEV (Miner Extractable Value) attacks.
4. Time-locked Transactions (less common in DeFi)